Always-on data encryption
Do I really need certificates across my whole digital real estate?
Yes
To prevent hackers and scammers from ripping off your customers, you need to close all the doors – not just the front door.
Is this a turnkey solution? Yes, we manage the certificates across your whole digital real estate and we have a track record of doing so for some of the world’s largest and most complex organisations.
The Trustify Root and Chain of Trust
The Trustify story starts with 25 years of Senior Management Team experience in designing, building and managing complex PKI requirements for many of the world’s leading brands.
This critical insight, including many times being called-in to recover failing PKI projects, has led the Management Team drive a new approach to delivering Managed Certificate Services centred on laying the right foundation on which to build good Digital Trust through PKI Automation.
This Root and Chain of Trust is the DNA running right through our new suite of Managed Certificate Services designed and built with key Partner vendors including DigiCert, Gemalto and Mocana.
New managed services not yet seen by the market and offering Enterprise Organisations the ability to reduced Total Cost of Ownership, increase Operational Efficiency and certainty, and massively reduce business risk across every user, device authentication or data encryption requirement.



Scale & Resilience
Our highly scalable and resilient certificate service platform is capable of serving multiple user, device, endpoint encryption and authentication services to your organisation 24/7/365.
So why chose Trustify?
Many organisations have selected Trustify for 2 main reasons:
- Certainty of Delivery
- Cost Savings
With Blockchain Technology not yet delivering real PKI systems replacement, many organisations are turning to innovations in PKI Automation to protect the next 5 to 10 year horizon. Trustify has developed the best of these.
The Trustify Root and Chain of Trust
Multi-CA and Multi-Tenant capabilities are now available in the form of a fully Managed Certificate Service in the UK, EMEA, North America and Asia.
For the first time organisations can drive centralised Policy & Compliance, Provisioning, Lifecycle Management & Monitoring from one service platform manned by Experts.
DX Project Risk disappears as services get delivered ahead of expectation and for less money than before.
Predictably Lower Costs
Trustify can supply this Managed Security Service breakthrough on fixed annual cost basis or on variable consumption rates.
Pay per Certificate or All You Can Eat.
So how do we deliver for you?
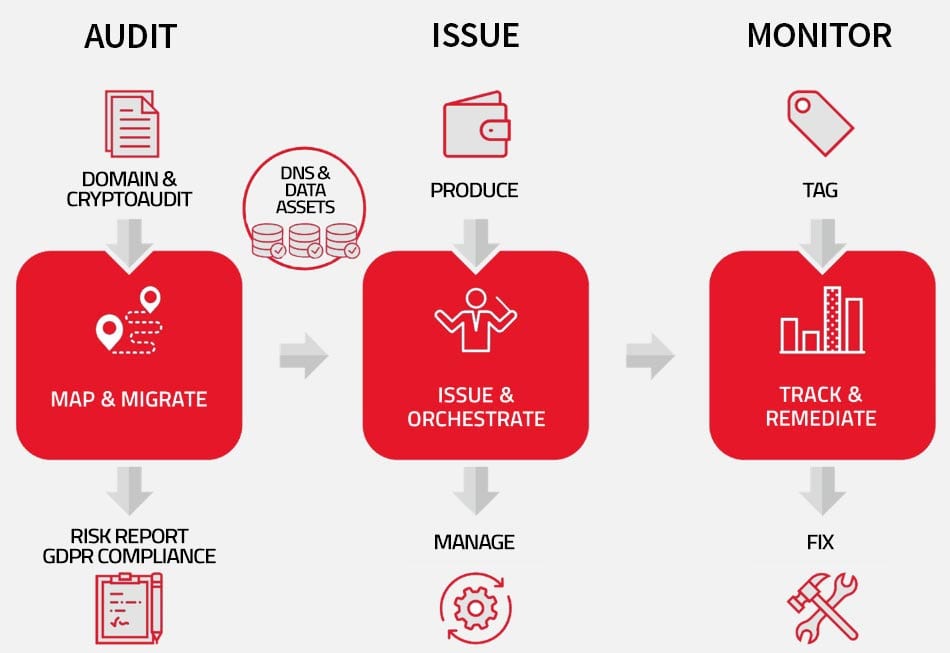
Our Discovery process is swift and cost-effective and is proven to out-perform the market leader in certificate orchestration services used to over-selling Certificate Discovery Services as a full-cycle Certificate provisioning system.
Trustify’s upfront Crypto Audit service offers a highly accurate Endpoint Discovery capability capable of identifying any unprotected external or internal domain and using unique automation AI to enrol and protect the endpoint.
This service automation innovation is implemented as part of a comprehensive Service Plan. We can accommodate legacy certificate platforms or swap them out with lower cost options.
Our Managed Service options include fully outsourced 1, 3 or 5-year plans or we can provide you with the platform, the management console and the training to DIY the service.
You chose, to fit your operational service requirements.
How does it compare to standing-up self-managed PKI Services?
You decide. We can deliver a fully managed, multi-CA, multi-location, Managed Service for volume users at $10/€9/£8 per annum for Enterprise Certificates including User, Device, S/MIME, Document Signing and SSL/TLS.
We can also go as low as $1/€0.9/£0.8 for IoT Security Certificates for SCADA, Smart device or Sensor requirements.
Compare this to spending upwards of $5million* to stand-up a PKI instance with no project delivery certainty and no guaranteed SLAs over the long-term.
Added-value
Our new Managed Certificate Service includes Digital Brand services. We have added the ability to centralise the management of all Domains, Public CA SSL certificate requirements and DNS Risk as part of our platform.
We can also blend and adapt 3rd Party services (over time) to accommodate changes in your circumstances.
We provide staff training and reporting and compliance tools to keep you secure and informed.
A Safe Pair of Hands
So, consider our service when you hear your colleagues agonising over how to refresh your certificate estate or issue mobile device certificates to BYOD devices when you know you don’t have the expertise in-house to design, build or operate reliable PKI services.
Proven TCO
They are all served by the Trustify AIM innovation
We deliver an average saving of 65% over standing-up PKI services on a DBFO basis.
Now that you know about our Managed Certificate Services you have to get a quote
Our self-service options include offering a choice of Public CA providers to cover any Enterprise CA requirement. We offer 2x Trustify Commercial Roots, and we can integrate any Root CA of your choice including Microsoft:
- Our own Trustcubes ICA with LEI built-in
- DigiCert CA
We give you Managed Service or Self-service options regardless of the size or your organisation.
Why not book a Service Demonstration now
Download our Certificate Services brochure

For SMEs
We provide products for start-ups and smaller organisations including accountants, insurers and retailers, medium-sized law firms and financial services companies, for schools and biotechs.
For Enterprises
We’re trusted to solve Cybersecurity issues for major organisations across the public, insurance, financial services, legal, pharmaceutical and accountancy sectors.
For SMEs
We provide products for start-ups and smaller accountants, insurers and retailers, medium-sized law firms and financial services companies, for schools and biotechs.
For Enterprise
We’re trusted to solve Cybersecurity challenges for major organisations across the public, insurance, financial services, legal, pharmaceutical and accountancy sectors.


